Ever wondered what a VPN is and how does it work? With lots of advertisements & promotions, you might have already come across many YouTubers or websites promoting at least one VPN service.
In this article, we’ll try to understand how VPN works under the hood.
What is a VPN?
A VPN (Virtual Private Network) extends a private network over the public (e.g. internet) or any other shared network.
It allows a user’s device to be part of a remote private network over any public network, using a Tunneling Protocol. These tunnel implementations are mostly encrypted for security reasons, although encryption is not inherent to VPN.
An overview of VPN
VPN uses two components to establish a tunnel over the public or shared network – The VPN Client and The VPN Server.
The VPN client software can be installed & configured (tunneling protocol, authentication, etc.) at the device level (laptop, desktop, mobile, etc.) or router level. With a router level VPN configuration, all traffic from (router) connected devices (including smart TVs, gaming console) to the public or shared network goes via the VPN.
On the other hand, the server configurations are handled by the VPN service provider. These configurations can vary depending on the requirements to support different tunneling protocols, policy, authentication method, support of rotational or static public IP to name a few.
Types of VPN
VPNs can be broadly divided into two categories.
- Client-based VPN
- Network-based VPN
Client-based VPN
A client-based VPN allows a user device to be part of a remote private network. Here, the VPN client needs to be configured at the device level to establish the tunnel to the remote private network.
Primary use cases of client-based VPN:
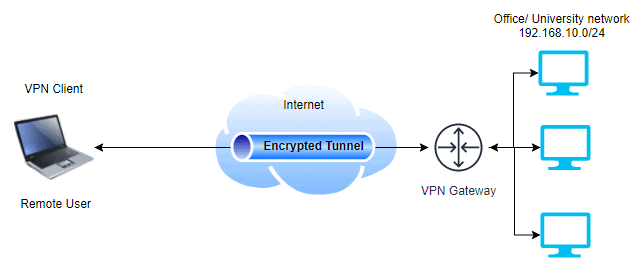
- An employee working from home accessing the company’s private network securely over the Internet.
- Devices using any commercial VPN services to access the internet. This type is generally used for communicating over untrusted wifi networks in airports, coffee shops, etc. Any communication via unencrypted protocol (e.g. HTTP) over these untrusted networks can easily be intercepted. Even for HTTPS traffic, (unencrypted) DNS queries over the network could be intercepted as well, exposing a list of accessed domains that a client visited. VPN generally encrypts all the traffic to the VPN server by default and forwards* it to the intended destination server. It reduces the probability of man-in-the-middle attacks over untrusted wifi networks.
*Note: If encryption isn’t supported by the destination server, a VPN cannot provide end-to-end encryption from the client device to the destination server. In this case, the VPN tunnel will encrypt the data from the client device to the VPN server, decrypt it on the VPN server, and then forward the unencrypted data to the destination server.
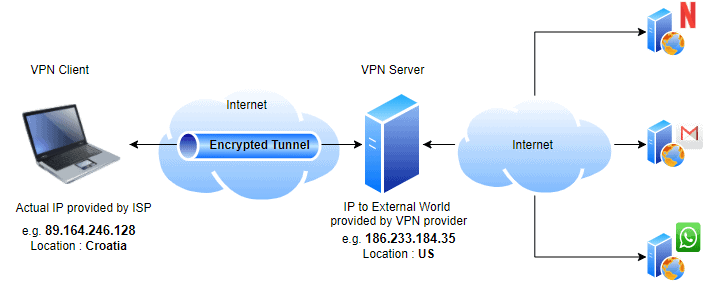
As seen in the example, the proxy IP (“186.233.184.35”) Address assigned by the VPN provider acts as the user’s public IP, hence hiding the public IP (“89.164.246.128”) provided by ISP (Internet Service Provider) from the outside world (Google, Netflix, Facebook, etc.). Thus, it can also be used to bypass geo-restricted content.
The encrypted tunnel even makes it possible to bypass Internet Censorship, by bypassing ISP-specific rules that may have been imposed by the local authorities.
Network-based VPN
Network-based VPNs are used to connect two or more private networks over the Internet rather than using a direct (physical) private connection.
Here the configuration is handled as part of the edge router / VPN gateways at both the private networks.
Primary use case of Network-based VPN:
Two corporate offices are separated by location to connect to each other as part of a single private network.
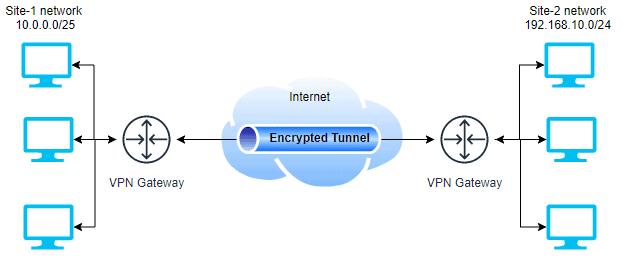
As seen in the example, a user at Site-1 can communicate with network resources present in Site-2 as if it is part of Site-1 private network.
VPN Anonymity, Security, and Privacy
Privacy is the most advertised feature of many commercial VPN services, which many people confuse with Anonymity.
VPN acts as a centralized middleman between the client and the destination server. Even though the VPN hides the client’s IP from the destination server, the VPN provider itself knows the client’s IP, along with a few additional device info. A VPN, thus, cannot provide true anonymity by design.
But, what about privacy? Nowadays, almost all web communications are encrypted by default using HTTPS. If you connect to an HTTPS website (without VPN), the communications between you and the website cannot be intercepted by any third-party, including your ISP. All your ISP knows is the set of domain names resolved by the ISP’s DNS, which are mostly un-encrypted. The ISP might sell this data to advertisers, or the data may be stolen in the course of an attack on the ISP’s servers.
But the same holds true for VPN as well. The communication between a website and the client remains encrypted over a secure protocol, such as HTTPS; the information about your web activity that was earlier known to the ISP is now known by the VPN provider instead. A VPN provider’s claim of ‘No-Log’ policy can only be termed as “privacy by policy” as there is no way for individuals to verify or refute this claim. Whether VPNs indeed provide better privacy compared to ISPs, is heavily dependent on specific situations or use cases.
If you reside in a country where strong data privacy and protection laws are applicable, your Government might prevent ISPs from logging your domain information. In such cases, your privacy is protected even without a VPN. On the other hand, a VPN provider based out of China is bound by law to share user information with the Government, if asked.