Over the years, the online advertising industry has suffered from several instances of ad fraud, especially the unauthorized sale of ad inventory through techniques like domain spoofing. To counter this, in 2017, IAB introduced a new protocol to fight against such illegitimate practices, in the form of ads.txt (short for Authorized Digital Resellers).
With ads.txt, publishers can authorize specific sellers to sell their ad inventories. If any unauthorized seller tries to sell the publisher’s ad inventory, the impressions will automatically be invalid.
But that didn’t stop fraudsters from selling fake ad inventories. Soon after, a few workarounds were in practice. And there have been multiple reports of new bot-driven manipulations to sell unauthorized ad inventories and generate fake views.
References:
#1 Fraudsters manipulated ads.txt to sell fake inventory – DoubleVerify Fraud Lab
#2 The latest ads.txt fraud: the 404bot
Still, researchers (DoubleVerify, Integral Ad Science, etc.) in ad tech can identify patterns in such bot-based ad frauds at an early stage and take actionable measures to block them.
However, there is now an entirely new type of digital ad fraud making the rounds, which affects not only the advertisers but the web community as a whole.
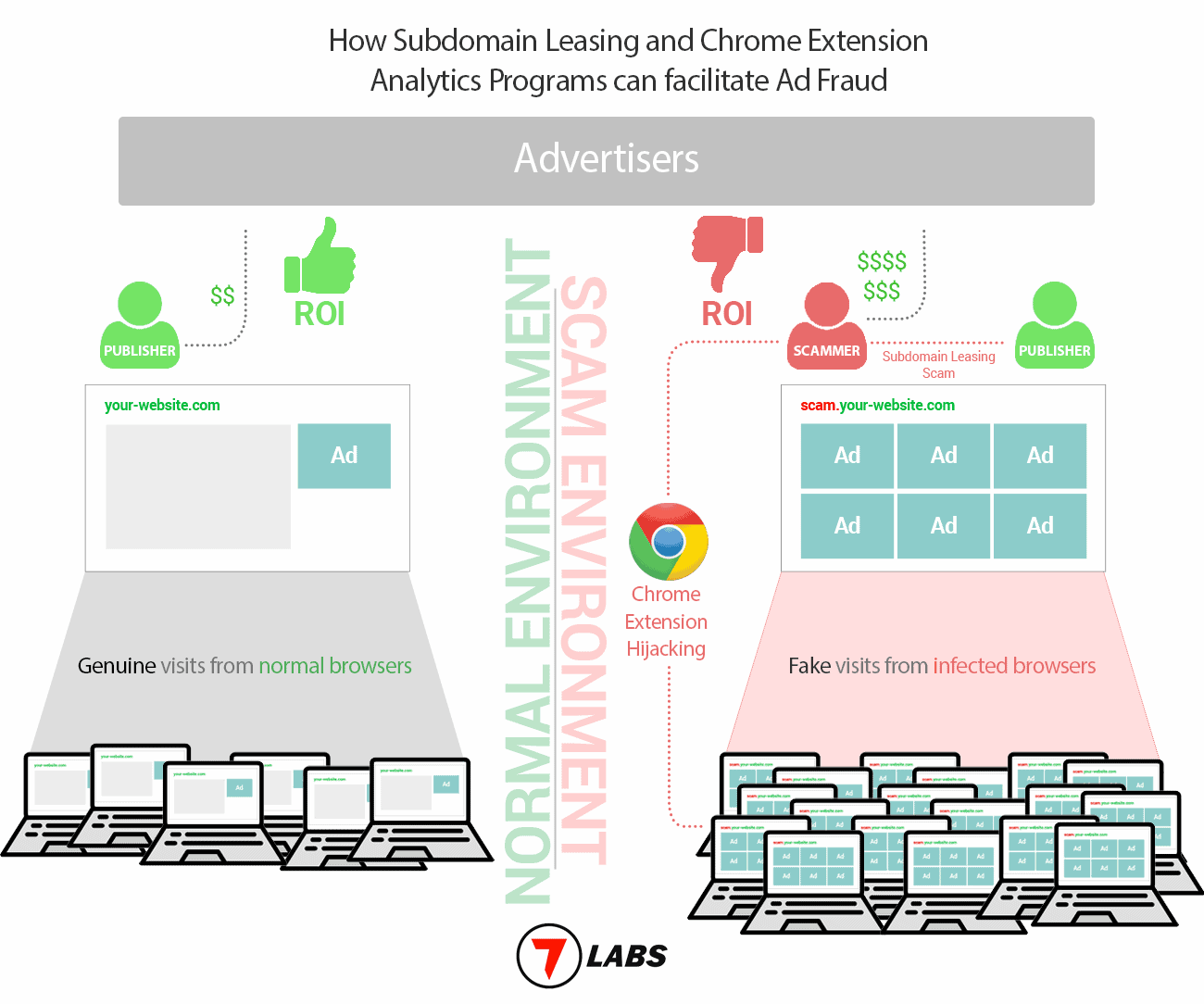
We recently fell victim to a scam operation and discovered the bigger picture while doing our research. This novel ad fraud operates on three levels.
Subdomain Leasing or Domain Takeover
The perpetrator generally approaches small & mid-size publishers with decent domain authority, convincing them to participate in a seemingly beneficial subdomain leasing program. Publishers are lured into thinking that the subdomain leasing program is safe for them as well as a decent passive income stream.
As a part of the onboarding process, the perpetrator convinces the publisher to provide them control over the leased subdomain by updating their CNAME records, as well as sharing the Google Analytics Breakdown report for the domain. Additionally, they also instruct the publisher to update the ads.txt file of the root domain with a list of sellers of the perpetrator’s choice.
Small & mid-sized publishers usually don’t manage their own ad inventory and rely on third-party advertising programs. As a result, they may not be aware of programmatic advertising and associated frauds. The perpetrator takes advantage of this situation and easily persuades the publishers to act in their favor.
In worse cases, the perpetrator manipulates the site owners to hand over the ownership of entire domains. Either way, they manage to take control of the domain’s ad inventory.
References:
#1 Why you should think twice before leasing a subdomain
#2 Suspicious Takeover of Websites like DroidViews.com
Securing Fixed CPM rates from advertisers
With the domain’s Google Analytics Breakdown Report and its ads.txt under control, the perpetrator now approaches the sellers (via ad management companies), and secures fixed CPM rates for the domain’s inventory.
Generating views in millions via browser hijacking
At this point, the perpetrator has secured ads at fixed Cost per Mille (CPM) pricing and also has the control to run them on the publisher’s domain or subdomain (via domain takeover or subdomain leasing). The only remaining piece now is to channel visitors and generate views.
Alongside subdomain leasing, the perpetrator runs a data analytics program, which claims to collect anonymous data from Chrome extensions to conduct research & gain marketing insights.
They convince multiple Chrome extension developers to integrate an analytics script called “script.js” in exchange for monthly payments.
The script reaches the users’ computer via automatic extension updates. And once activated, it reportedly opens pages in the background from various domains & subdomains in (1), generating fake/invalid views.
As per our estimates based on the data we’ve collected, the script has already reached millions of computers, by infecting several popular Chrome extensions.
References:
#1 Browser Hijacking with Chrome extensions
#2 Chrome seems to randomly open windows I can’t view
#3 Multiple Extensions are Compromised in a Browser Hijacking
#4 Chrome Keeps opening up new chrome pages from 7labs.io
#5 Windows in the background inaccessible
The full-scale of this operation impacts three key players of the web community.
The publisher leasing the subdomain gets a bad reputation from visitors when they start to report suspicious activity linked to their domains. And since the generated views are all fake, the advertisers eventually realize that the Click Through Rate (CTR) is extremely low, and blacklist the domain.
The perpetrator scams the advertising industry in millions of dollars by generating fake views that have no ROI.
Chrome developers also get the ax eventually. When users start noticing malicious activity linked to their extensions, the developers stand to lose a significant part of their userbase.
Publishers and extension developers thus both bear the brunt of the situation, and they may not even realize it until too late.
Based on our firsthand experience and various other reports, a particular New York-based individual is allegedly responsible (or associated with) for the entire operation.
We want to protect the web community from such type of scams, as they impact all of us. The intention of this content is to raise awareness among publishers and developers, as well as other key players of the ad-tech industry.
If you want to explore more about the situation and require additional details, we would be happy to provide you with more information. You may contact us at 0b111[at]7labsofficial.com