You might already be familiar with the fact that the best way to store your crypto-assets securely, is by using a hardware wallet. And if you’re recently planning to get one, you might have already narrowed your choice down to two of the popular options available in the market — TREZOR or Ledger.

Generally, if you’re researching on the Internet about these h/w wallets, you’ll likely get the initial impression that both TREZOR and Ledger offer you the same set of features and level of security. You might just think that it’s a matter of personal choice that helps you determine which hardware wallet you pick in the end. But is it really the case?
How do hardware wallets work?
In simple terms, hardware wallets offer a cold storage solution for storing your crypto-assets securely. Your wallet’s private keys are generated and stored offline in a micro-controller. To complete a transaction, the wallet sends a signed message to your computer or smartphone (where the transaction is initiated), without being connected itself to the Internet at any time. The private keys are never supposed to leave their isolated storage element.
Moreover, the private keys are never openly displayed to the user. In order to access a hardware wallet, the user needs to enter a 4 to 8 digit PIN. If the PIN isn’t entered correctly for a specific number of times (usually three), the wallet automatically resets itself, erasing all the data in it. This mechanism protects the device from brute force entry, should it fall into the wrong hands at any point of time.
The key to recovering or restoring the wallet back to its previous state is to provide the wallet seed — a 12 or 24 word sequence — which is presented to the user only once during the creation of a new wallet. The user is expected to memorize and securely store this seed.
This is the working principle on which both TREZOR and Ledger are based upon. And from a high level view, they both seem similar and secure. But a closer look at the implementation reveals some significant differences between the two wallets.
Hardware implementation of TREZOR and Ledger
Both TREZOR and Ledger h/w wallets are USB powered devices, having two physical buttons (for confirming transactions and navigating through the wallet interface), and an LCD screen for displaying information. But this is, more or less, the point where the similarities end between the two devices.

On the inside, the TREZOR uses a standard ARM Cortex M3 32-bit micro-controller (STM32F205) for generating and storing the private keys. This is a general purpose MCU that is neither secure, not contains any sort of secure enclave. It also has an external clock, which is exposed and vulnerable to tampering. This means that the device is vulnerable to hardware-based attacks, which isn’t good news if it falls into the wrong hands.
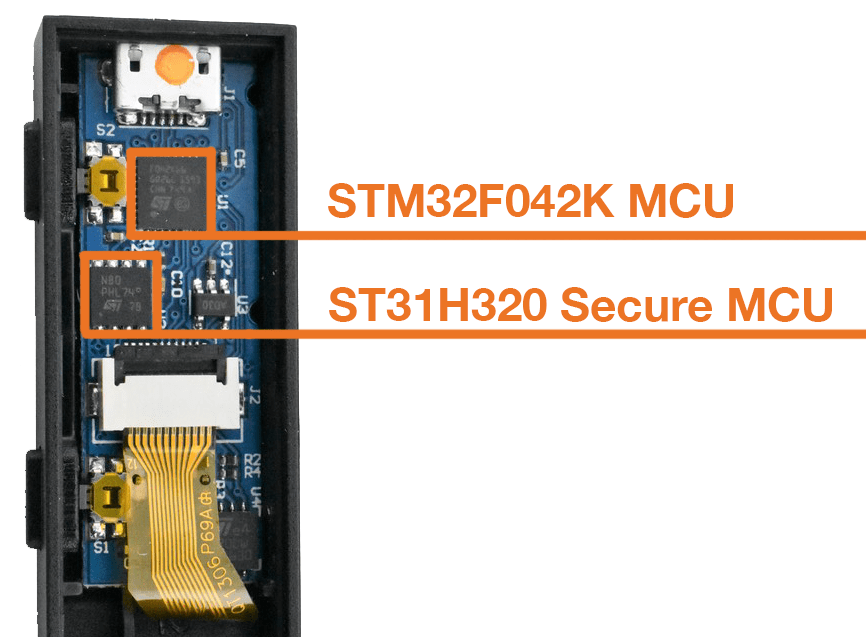
The Ledger, on the other hand, uses two MCUs instead of just one. The first one is a standard MCU (STM32F042K) very similar to the one used in TREZOR; the only difference being that this one uses an internal clock, rather than an external one. However, the second MCU (ST31H320) used in Ledger is a proper bank-grade secure enclave, which is used to generate and store the private keys
 .
.
To be precise, Ledger’s secure enclave scores an EAL6+ common criteria (CC) certification, while the combined dual MCU architecture has a lower EAL5+ certification, which is not bad either. It should be noted here that the non-secure standard MCU in Ledger is only used for temporary storage, and does not have access to the secure enclave. The TREZOR does not meet any CC certification, as it doesn’t have a secure enclave.
But what are the implications of not having a secure enclave in a hardware wallet? In the following section, we’ll compare the two wallets head to head, and try to explain how the Ledger is more secure and better option of the two.
Why Ledger Nano S is better than the TREZOR
Let’s analyze the two wallets, by studying their behavior against certain factors as described below.
The Man in the Middle (MIM) attack
Ledger Nano S is essentially one of the second generation of Ledger devices developed by the parent company called Ledger. One of the significant differences between the second generation Nano S and the first generation Nano, is the fact that the original Nano was a simple USB drive without any LCD screens or buttons. This fact exposed the device to a certain type of possible vulnerability, known as man in the middle (MIM) attack.
Because the Ledger Nano had no display or buttons of its own, all the interactions involving your Ledger wallet (including initial setup, sending and receiving funds) had to be carried out on the computer. This meant that certain private information, such as, displaying of the wallet seed, or setting up/providing the Wallet PIN, were handled on a computer, rather than the device.
Now, if your computer was somehow compromised, there was a significant possibility that your wallet interactions were monitored by third parties, and at a later time replicated to steal your funds.

The TREZOR did not suffer from this vulnerability, since it had a display screen and physical buttons of its own. All private wallet-related information could thus be directly handled on the device, instead of relying on another external device or display.
However, the next generation of Ledger devices fixed the issue by providing a display screen and two hardware buttons for direct interaction, similar to that on the TREZOR.
Note: From here on, although we’ll be focussing mainly on the Ledger Nano S, it should be noted that both the second generation Ledger devices — the Ledger Nano S and the Ledger Blue — are built upon the same dual MCU-based architecture, and thus have the same level of security.

There was another kind of possible MIM attack, which the Nano S was vulnerable to in the past, but has since been fixed via a firmware update. In this attack, the sender’s computer can be compromised in such a way that the recipient address in a transaction is somehow altered with a similar looking address, which belongs to a third party.
Up until recently, even with the device’s screen, the Ledger Nano S only displayed the first 4 and last 4 characters of the recipient’s address, prior to confirming the transaction. Technically, a perpetrator could create a similar looking address of his own, containing the same first 4 and last 4 characters, as the original recipient’s address. Then, he could use your compromised computer to switch the recipient’s original address with the counterfeit address, when you’re initiating a new transaction.
While authorizing the transaction, since the Ledger would display only the 8 matching characters while signing the transaction, you might not be able to tell them apart and confirm it anyway. In that case, the funds would reach the counterfeit address, instead of the intended recipient.
The current cost of generating an 8-position specific, case sensitive address, using a vanity address generator, is roughly $800. This cost could be further brought down to $30 for generating an address with 7 specific characters instead of 8, something which is quite easy to miss if you aren’t careful enough.
Note: This type of attack is particularly effective when the transaction amount is significantly higher compared to the cost of creating such vanity addresses.
While the TREZOR did not suffer from this vulnerability to begin with, the Ledger team has since fixed this issue via a firmware upgrade. Both the TREZOR and the Ledger now display the entire wallet address of the recipient, while signing a transaction.
The above MIM attack vulnerabilities are probably the only reasons why the TREZOR would be considered a better hardware wallet over the Ledger. But, since the Ledger team has addressed both of these issues — providing a display with the Nano S and a firmware upgrade (V 1.3.1 or above), which displays full bitcoin or altcoin addresses on the Nano S — this argument no longer holds true.
Potential backdoor in hardware implementation
We’ve already mentioned that the Ledger wallet uses a bank-grade secure enclave for generating and storing private keys, while the TREZOR does not. Instead, the TREZOR stores private keys in a general purpose MCU, which can be hacked into, with the help of specific knowledge and tools.
This means that if a TREZOR wallet falls into the wrong hands, the data stored within the device is practically feasible to be extracted, as it offers arguably no security at the hardware level. Moreover, it might also be possible to steal the private keys remotely with the help of malicious code executed during the device firmware upgrade. Several demonstrations have shown that one could retrieve the private keys from a general purpose MCU such as TREZOR’s, without even having to know the device PIN.
The TREZOR’s security woes don’t end just there. Since the TREZOR’s firmware and software are fully open source, anyone could create a counterfeit copy of the TREZOR wallet, running a modified version of firmware that is programmed to remotely steal your private keys.
This sort of counterfeiting can occur anywhere in the product’s supply chain, and there’s no way to check the integrity of the device once it reaches the consumer — except for an anti-tampering sticker attached to the package.

On the other hand, the Ledger wallet does not require an anti-tampering sticker, as a cryptographic mechanism, known as attestation, inherently prevents tampering of the device. Each time a Ledger device is connected to a computer, the Ledger client sends a random value to the device as a challenge.
The Ledger device, then signs this random value, along with the firmware version, using an embedded private key residing in the secure enclave. The client can verify this signature as it knows the public key. There is no way for an attacker to tamper with the hardware or replace the firmware, and bypass attestation without knowing the private key.
Update: TREZOR has released a new iteration of the original, known as the TREZOR Model T. And even though its technical specifications are yet to be published, the device still ships with an anti-tampering sticker.

Platform Support
Even though the Ledger’s software applications (wallets) are open source, the firmware and other components are closed, and governed by its manufacturers. Moreover, the company is actively working to improve their product, ensuring faster and more reliable firmware updates, additional support for more alt-coins on a weekly or monthly basis. They have recently partnered with Intel to provide consumers with more innovative Blockchain-based solutions.
The TREZOR, on the other hand, is still largely community driven. Being fully open source also helps attackers to easily look for potential exploits in the implementation. The TREZOR does still get regular firmware upgrades, adding support for new cryptocurrencies as they arrive, but at a relatively slower rate as compared to Ledger devices.
As an icing on the cake, it’s quite surprising to note that arguably the best hardware wallet available in the market, is in fact, also the cheapest!
We hope that the above points will help you determine the better of the two hardware wallets. And, if you have persuaded yourself to buy a Ledger wallet, you can order one right now from the below link.
It should be noted that hardware wallets like Ledger, while being secure, is still prone to attacks targeting user errors. A user should always be careful when it comes to handling cryptocurrency wallets. When you use a hardware wallet for the first time, make sure you set it up yourself, generate the wallet seed, and store that seed in a secure place. Also, ensure that you verify the complete recipient address from the wallet’s display before confirming a transaction.