If you deal with cryptocurrencies, you might already be aware of the fact that hardware wallets are the best way to store them securely. And looking at the hardware wallet landscape right now, there are primarily two major players that you could choose from — TREZOR or Ledger.

While the TREZOR is completely open source, the Ledger runs their own proprietary firmware beneath open source apps. Apart from that, both the hardware wallets seem to offer similar features and security. So which one do you go for? Is it just a matter of personal preference, or something more?
How do hardware wallets work?
Cryptocurrency wallets usually fall into two wide categories. On one side, there are hot wallets (like Jaxx, Exodus, etc.), which facilitate ease in performing transactions. But they are also prone to frequent attacks as they are always connected to the blockchain/Internet.
Cold wallets (such as paper wallet), on the other hand, mostly stay offline, disconnected from the blockchain, and isolated from any network (hence the term “cold”). These wallets are ideal for storing crypto assets securely over the long term, without performing any transactions.

Hardware wallets offer a best-of-both-worlds solution, by providing the ease of transactions of hot wallets, while maintaining the security of cold ones. These wallets generate and store the wallet’s private keys in a micro-controller, and are never supposed to reveal them to any external component. To complete a transaction, the wallet sends a signed message to your computer or smartphone (where the transaction is initiated), without itself being connected to the Internet at any time.
Moreover, the private keys are never openly displayed to the user. In order to access a hardware wallet, the user needs to enter a 4 to 8 digit PIN. If the PIN isn’t entered correctly for a specific number of times (usually three), the wallet automatically resets itself, erasing all the data in it. This mechanism protects the device from brute force entry, should it fall into the wrong hands at any point of time.
The key to recovering or restoring the wallet back to its previous state is to provide the wallet seed — a 12 or 24 word sequence — which is presented to the user only once during the creation of a new wallet. The user is expected to memorize and securely store this seed.
This is the underlying principle on which both TREZOR and Ledger are based upon, and on the surface, nothing much seems different. Both hardware wallets are USB powered devices, consisting of a trusted display and on-device buttons for confirmation or denial of signing transactions.
But a closer look on the inside reveals some significant differences in the hardware and implementation of the two h/w wallets.
Hardware implementation of TREZOR and Ledger
Both the original TREZOR One, and the new TREZOR Model T are built on a single-chip architecture, and use a standard ARM Cortex M 32-bit general purpose micro-controller (STM32F205 for TREZOR One and STM32F427 for TREZOR T) for generating and storing the private keys.

The Ledger Nano S, on the other hand, uses a dual chip architecture. The first one is a general purpose 32 bit micro-controller (STM32F042K) similar to the one found in TREZOR; the second one is a bank grade Secure Element (ST31H320), which is primarily used for storing the private keys.
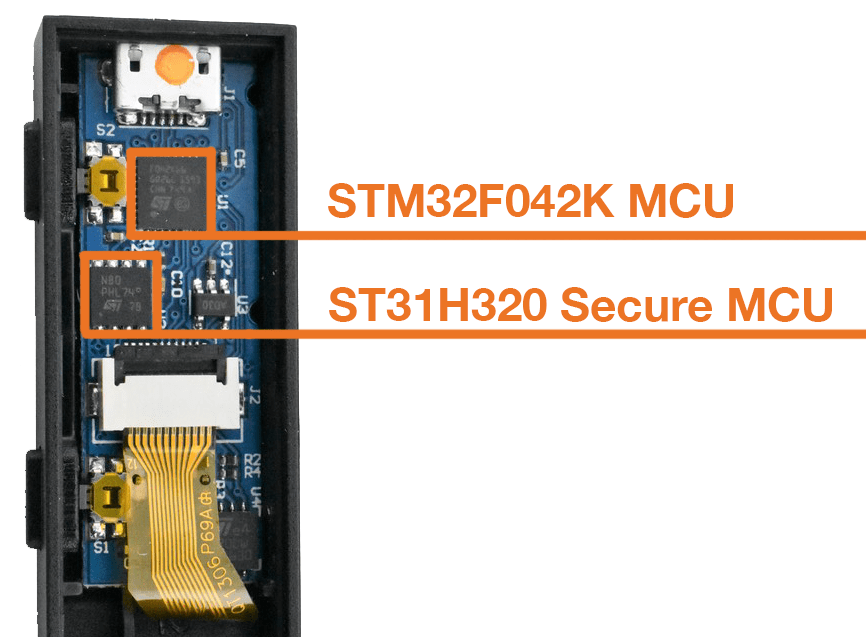
The Secure Element (SE) on the Ledger scores an EAL6+ common criteria (CC) certification, while the combined dual chip architecture has a lower EAL5+ certification. Such a certification is not applicable for the TREZOR devices, as they do not have a Secure Enclave.
Generally, the ST31 SE, by design, is less prone to hardware-based attacks, compared to general purpose MCUs, like the STM32 micro-controllers. Security researchers have been able to establish in the past that the security scheme of STM32 series MCU is more vulnerable to fault attacks like this one.
But there is, in fact, more to the story.
Secure Hardware and Open Source
The choice between secure hardware and open source has been a long standing debate, which has repeatedly cropped up in a number of occasions. Between the TREZOR and the Ledger, the TREZOR fully embraces the open source ideology; it does not implement any closed or secret components (such as a secure enclave), and uses open source firmware & apps.
Ledger, on the other hand, believes that a secret hardware component (i.e., the Secure Element) offers better security compared to a general purpose MCU with open-source software. And, by restricting access to certain parts of the hardware and software, the integrity of the SE can be maintained; hence protecting its secrets from extraction, as well as preventing its key operations from being compromised.
Now, there are both pros and cons to each one’s approach.
TREZOR’s implementation, firmware and apps are publicly available, and enables rigorous peer reviews within the developer community. This allows better discovery of potential loopholes or bugs in the implementation, enabling the community to develop suitable fixes quickly.
But, this also potentially exposes the key aspects of TREZOR’s design and implementation, including the details that are better kept secret, opening the door for possible exploitation of the vulnerabilities discovered in the system.
On the other hand, Ledger’s approach makes it difficult to carry out hardware-based attacks on the Secure Element, as the under-the-hood implementation of the SE, along with parts of the Ledger firmware, are not made available to the general public.
But, any possible vulnerability or security loophole within the SE, or the firmware would also likely remain hidden from the developer community, slowing down the rate of discovering vulnerabilities and providing suitable fixes.
In fact, many experts have often criticized such strategy of providing security through obscurity, as users have to trust the parent company for the correct implementation of hardware and software, without having the complete knowledge of it.
And though STMicroelectonics (the company which manufactures the SE) may also endorse a such philosophy, Ledger has shown its willingness to embrace open source elements as well; all of the apps that run on the Ledger devices are open source, and according to Ledger CTO, most of the firmware will also be in the future.
However, it’s not denying the fact that Ledger is not always upfront and clear on details, as and when new vulnerabilities are discovered. And according to Ledger, this is done in order to minimize the knowledge of these vulnerabilities and prevent potential attackers from exploiting them.
TREZOR and Ledger stack up against different attack vectors
Hardware wallets, like TREZOR and Ledger need to prevent a wide variety of attacks, which can be divided into two broad categories:
Remote Attacks — When an attacker attempts to potentially steal your wallet secrets and/or crypto assets by compromising your system remotely.
Direct/Physical Attacks — When an attacker is somehow able to get physical access to your hardware wallet, and tampers with the hardware and/or software of the device.
Ideally, both TREZOR and Ledger hardware wallets protect against remote attacks by design. The private keys are securely stored within the hardware wallet, never exposing them to the computer or smartphone that it is connected to. In order to perform a transaction, the user can verify the recipient address from the wallet’s display and then use the on-device buttons to confirm or decline the transaction. All that the connected computer or smartphone receives, is a signed message.

Thus, even if your system (computer or smartphone) is infected for a remote attack, your crypto assets are safe with TREZOR or Ledger, as long as these h/w wallets are untampered.
But, if the hardware or firmware in TREZOR or Ledger gets compromised, the device becomes vulnerable to a ton of other attacks. This could further happen in two ways:
Supply Chain Attacks — When the device is compromised (somewhere along the supply chain) even before you have set up your wallet.
Unauthorized Physical Access — When an attacker gains access to your wallet after you’ve completed the initial setup.
TREZOR and Ledger have both taken different steps to prevent supply chain attacks. TREZOR uses tamper-evident seals in the packaging to indicate possible breaches in the supply chain. If the seal is broken, it could indicate that the device inside might have been compromised. Moreover, the body of TREZOR devices are sealed using industrial glue, which makes it difficult for attackers to put the unit back together after making any possible alterations to the hardware.

The Ledger has a trusted computing base built around the Secure Element, which can be validated via cryptographic proofs. Any user can verify the integrity of a Ledger device by performing an attestation check. Moreover, each time a Ledger device is connected to a computer, the Ledger app on the computer (which is basically a Chrome extension) automatically checks for its integrity, and allows users to proceed only if attestation is done successfully.

This is how both TREZOR and Ledger employ countermeasures against supply chain attacks. But then, a situation may also arise where a malicious third party gains unauthorized physical access to your hardware wallet after you’ve set up the device. This could be done in two possible ways:
Theft — in which case, the hardware wallet is permanently stolen from you.
Evil Maid Attack — where an unauthorized person may temporarily gain physical access to your hardware wallet without your knowledge, and possibly compromise the device.
If the attacker steals your hardware wallet, they have a longer duration of time to perform an attack, and also possible access to expensive lab equipment.
In this regard, both the TREZOR and the Ledger have suitable countermeasures in place. The first level of protection offered by both, is having a secret PIN, without which an attacker won’t be able to gain access to the wallet contents through its user interface. And, in order to prevent brute force attack, these wallets are programmed to reset themselves and wipe all contents if the wrong PIN is entered repeatedly for a specific number of times.

Second, both hardware wallets use industry-grade encryption to protect against potential extraction of private keys via physical attacks. Additionally, the Ledger stores its private keys in a bank-grade Secure Element.
But, there could also be an “evil maid”, who has less time to perform an attack, and also without possible access to expensive lab equipment. In that case, he or she could temporarily gain access to your wallet, and compromise it to trick you into giving away its secrets.
Up until recently, it was almost impossible to know whether a TREZOR device is running a genuine software. An attacker could take advantage of this fact and push a compromised version of software, while hiding it to the user.
But with the latest update, the firmware (version 1.6.1), now checks the authenticity of the bootloader. The bootloader, in turn, also checks the firmware signature, making sure that both software parts are running genuine code. Moreover, the Memory Protection Unit (MPU) inside TREZOR now enforces write-protection on the MCU in such a way that only a firmware signed by SatoshiLabs (TREZOR’s parent company) is allowed to modify sensitive parts of the memory.
Ledger also prevents potential evil maid attacks through its automated attestation check. Every time the wallet is connected to a computer or smartphone, the official Ledger Wallet apps help to detect potentially compromised hardware or software.
Real life attacks and their mitigation
Security researchers and attackers alike have subjected both TREZOR and Ledger devices to a wide variety of security exploits. Whenever a vulnerability has been discovered, both TREZOR and Ledger developers have provided quick and timely fixes via firmware updates for the respective issues. As an example, let’s explore a few of the security fixes provided by both TREZOR and Ledger in their latest firmware updates.
TREZOR’s vulnerability — Flawed bootloader write-protection
The STMicroelectronics chip STM32F205 used in the TREZOR One device contains a flaw, which effectively disables the write-protection employed to protect the bootloader of the device. This flaw in the chip allows an attacker to modify and replace the bootloader via a malicious firmware update, which may potentially compromise seed word generation. TREZOR further adds that this vulnerability does not enable private key extraction from wallets where seed set up has already been done.
TREZOR provided the following software-level updates to mitigate this hardware issue, and additionally provided a new way to verify the authenticity of the firmware:
- The flawed bootloader write-protection by STMicroelectronics was supplemented with write-protection enforced by the MPU (Memory Protection Unit).
- The new firmware now checks the authenticity of the bootloader and also updates the device’s bootloader to the latest version.
- The activated MPU also prevents code execution from memory.
According to the TREZOR blog:
“The solution is to supplement the flawed OPTION BYTES write-protection, using another available protection system, called MPU — the Memory Protection Unit (different part of the chip). Using this unit in the bootloader, we can specify which areas of memory can be accessed or not, effectively reaching the intended level of protection (the MPU restricts access to sensitive parts of the memory including the bootloader area and the FLASH_OPTCR register). STMicroelectronics confirmed that by using the MPU, the issue is resolved.”
Ledger’s vulnerability — MCU Fooling (and a few other vulnerabilities)
A sure way to verify the authenticity of Ledger firmware is by performing the attestation check. But a flaw in Ledger’s implementation allowed an attacker to load modified firmware on to the device and yet pass the attestation check. Ledger has a blog post explaining the vulnerability and the fixes applied, where it also clarifies that the vulnerability does not facilitate private key extraction in pre-configured wallets.
Essentially, Ledger’s way of attestation is to have the Secure Element ask the MCU to send the firmware code in order to verify it. If the firmware code was compromised, it would still have to include the official firmware in its entirety, so that the MCU could pass it on to the Secure Element for verification.
According to Ledger, the MCU didn’t have enough storage space available so as to include the entire official firmware as well as any malicious code. But security researcher Saleem Rashid explained in a detailed post how Ledger’s attestation system was flawed.
The Ledger MCU initially included its bootloader and firmware in separate sections of memory, and each of those sections included a part of the code (called compiler intrinsics), which was identical in all aspects. This raised the possibility of a potential code caving, which could essentially be used to hide malicious code within the official firmware.
Saleem’s approach was to modify the firmware in such a way that it replaced a copy of the compiler intrinsics with malicious code, and have it make a call to the bootloader’s intrinsics during the attestation check.
Having verified itself to the Secure Element (MCU Fooling), the malicious firmware code could now take advantage of the interfacing elements, including the hardware buttons on the Ledger and its display too.
This could essentially allow the malicious code to compromise seed word generation, display incorrect addresses on screen for confirmation, or even confirm transactions on behalf of the user.
The new firmware (version 1.4.1) provided by Ledger fixes the above mentioned vulnerabilities and automatically updates the boot loader to the latest version. The countermeasures implemented in this update include the following changes:
- The MCU code has been refactored preventing simple code caving.
- The signature verification is now enforced using two different mechanism;
– Address fetch randomization.
– Timing constraints preventing the MCU to “uncompress” data to send to the Secure Element. - Several CRC code and checks are added filling up the MCU memory and preventing the modification of the memory without detection.
Best practices for h/w wallet security
Below are a few best practices for using hardware wallets that will help you ensure the safety and security of your crypto-assets.
Ensure that your hardware wallet is genuine: Depending on the hardware wallet of your choice, there are several ways to check the integrity of the product. TREZOR devices have tamper-evident seals on the packaging, whereas Ledger devices rely on cryptographic attestation proof. Nevertheless, it’s recommended to always purchase these devices from the official stores, or any of the authorized resellers. In case the integrity check fails, do reach out to the official TREZOR and Ledger support to ask for a replacement.
Update the wallet to the latest firmware before using: If your device passes the integrity check, the next step is to connect the device to your computer and ensure that the latest firmware updates are installed. If a new update is available through the official channel, go ahead and install the same. This would overwrite outdated, possibly compromised firmware, and also ensure that the latest security fixes are applied to your device.
Setup your own wallet seed: It’s never a good idea to use a pre-configured wallet, as someone else might have access to the wallet seed, and thus, access to your wallet as well. So, go ahead and set up your own wallet seed. Also, the longer your wallet seed is, the better the security.
Use a strong wallet PIN: Finally, it’s always a good idea to have a strong PIN (preferably 8 characters long) in place. This will protect your wallet against potential brute force attacks.
If all the precautions are properly taken, in case of theft, you should have enough time to move out your funds to a different wallet before the attacker is able to access them, although that’s less likely to happen.
TREZOR or Ledger — Which one to choose
Both TREZOR and Ledger have come a long way from their initial releases, and at their current iteration, both the devices are quite strong in terms of security in their own way.
TREZOR endorses a fully open source ideology and implements a firmware-based security on top of known hardware.
Ledger takes a more closed-source approach by implementing a Secure Element. At the same time, users can verify various aspects of wallet operations via black-box testing, without having extensive knowledge of the system.
When it comes to modern computing devices, vulnerability finding and fixing is a never-ending chain. Hardware wallets are no exceptions. The idea is to gradually close all attack vectors. The current fixes provided by both TREZOR and Ledger, make a successful attack significantly more difficult to achieve. And at this rate, both companies look determined enough to continue support for their respective devices over the long term.
In the end, it comes down to your preference in the ideology that you want to be a part of. If you’re more inclined towards the open source philosophy that relies on a software-based security model, the TREZOR should be your ideal choice.
Alternatively, if you want to have a bank-grade secure enclave protecting the wallet secrets at the hardware level, and have no problems with a partially closed-source system, you should go for Ledger.
However, if you’re ready to go for either of the two, and don’t have any specific preference between secure hardware and open source, here are a few more points to consider.
Support for Altcoins and Pricing
Both TREZOR and Ledger support most of the popular cryptocurrencies, like Bitcoin, Litecoin and Ethereum. And at the time of this writing, the TREZOR’s list of supported cryptocurrencies includes:
- Bitcoin
- Bitcoin Cash
- Bitcoin Gold
- Litecoin
- Ethereum
- Ethereum Classic
- Dash
- Zcash
- Namecoin
- Dogecoin
- NEM
- Expanse
- UBIQ
- ERC-20 Tokens
In comparison, the Ledger offers support for a wider range of altcoins. The whole list of cryptocurrencies supported by Ledger includes:
- Bitcoin
- Bitcoin Cash
- Bitcoin Gold
- Digibyte
- HCash
- Qtum
- PIVX
- Vertcoin
- Viacoin
- Ubiq
- Expanse
- Dash
- Dogecoin
- Litecoin
- Ethereum
- Ethereum Classic
- Stratis
- Ripple
- Zcash
- Komodo
- PoSW
- Ark
- Neo
- Stellar
- Stealthcoin
- BTCP
- Zencash
- ERC-20 Tokens
Furthermore, the Ledger is available at a lower price point compared to the TREZOR. The original TREZOR One is available at a retail price of €89.00, while its successor, the TREZOR T, was priced at around €159.00 during the first batch of pre-orders. Compared to that, the Ledger Nano S is priced at €79.00 on the official website.
So, which hardware wallet would you finally go for? Let us know in the comments below.